Separation of Crime and State - Part 1

In this series of the Insecure Line we discuss the differences between hacking operations conducted by criminals and states. Hacking and cyber operations are inherently sinister, but in general, its easier to see the immorality of cyber criminals and the righteousness of governments. Criminals extort and steal, while governments hunt down criminals and terrorists. As tempting as it would be to get into the philosophy of hacking, that's not our domain. Instead, we will compare and contrast the criminal hacker versus the state-sponsored hacker. We will explore their similarities and differences in capabilities, intent, and ultimate impact on their victims, while leaving the question of morality to the readers and philosophers.
Background
News recently broke that WhatsApp has detected and notified users about potential targeting with spyware developed by Paragon, a mercenary spyware company founded by former Israeli intelligence officers. There are many companies like Paragon, some very well known, such as the infamous NSO Group and their pegasus spyware, and others less famous or entirely unknown. These companies, known as mercenary spyware developers, build hacking tools and systems that they sell to buyers around the world. They innocently claim that they only sell to "the good guys" however history shows this isn't true. There are several instances where the spyware built by these organisations has been found on the devices of journalists, activists, or other political opponents. The recent Paragon-WhatsApp news is simply another case of these tools being used against civil society.
This series of the Insecure Line was inspired by the account of one Italian journalist, Fancesco Cancellato, who was notified by WhatsApp that he was a target of the Paragon spyware. In his interview with TechCrunch, Cancellato was quoted as saying:
“You ask yourself, why me? This is the thing, I mean, what did they want from me? That’s the first question, the second question is what did they take from me? Where did they go? What did they do to me? Once they got into my phone, where there is basically my whole life, my vacations, my friendships, my family, my bank passwords, there is everything — my work stuff…”
Usually, for a victim of cyber crime, the question of "why me?" is largely irrelevant. Criminal hacking groups simply don't care who you are. They are opportunistic, going for the easiest target, the lowest hanging fruit - it is rarely personal. But for state actors, its quite the opposite, it's highly personal. So while a victim of cyber crime might be stressed and impacted in the short term, hopefully they can move on knowing they were just unlucky. Unfortunately the same doesn't apply to the victim of a state-sponsored cyber campaign. For one reason or another they have been deemed "important" enough to be targeted and that doesn't go away overnight.
In this multi-part series we explore why the impact on the victims of crime and state hacking is so different. To do so we need to look at their entire operation, starting with their capabilities.
Part 1: Capabilities
When we talk about capabilities, we are referring to the tools, techniques, and skills available to the threat actor. For example, the malware and exploits they use, their data processing capabilities, their access to other networks and systems, or general influence and control. Nation states have far superior capabilities compared to a criminal operation. They often have whole departments dedicated to cyber operations, such as the Unit 8200 of the Israeli signals intelligence (digital spy) agency, which is said to be the largest unit in the "Israeli Defence [sic] Force" or the well-known US agency the NSA.
In this edition, we will explore factors that allow states to build these large, sophisticated, capabilities and why criminal operations rarely reach the same level of capability.
Immunity
In most countries computer hacking is illegal and in some countries the definition of "hacking" is very broad, effectively criminalising all aspects of computer hacking. One of the primary factors that enables nation states and their cyber departments to build sophisticated capabilities is their immunity to prosecution. These agencies are part of the government and are thereby given special powers and authority to do activities that would otherwise be illegal. This means government cyber departments can work in plain sight.
Criminals on the other hand are working outside of the law and, therefore, have to work in secret and remain undetected. Growing too big can be their demise. There are some well-known large cyber criminal operations, such as the once notorious ransomware gang LockBit (that was ultimately dismantled). However, these operations don't have a large organisation, they instead rely on a large pool of dispersed "affiliates" who build the tools, gain access to networks, and run the operations. LockBit themselves have very little control over the affiliates and operate more as a ransomware-as-a-service provider. Essentially providing a platform, infrastructure, and some supporting services for their affiliates to deploy ransomware and extort their victims.
The immunity and special authorities given to government departments gives them the ability to plan and operate with long-term horizons. They can invest in research and development spanning several years, often aiming to solve unique challenges related to their cyber operations. For example, the famous malware dubbed STUXNET was discovered in 2010 and attributed to "causing substantial damage to the nuclear program of Iran" and was said to have been developed since at least 2005. STUXNET was so advanced that it was programmed specifically for the industrial control system that controlled the centrifuges in the Iranian nuclear facility. The diagram below, from the IEEE Spectrum article on the "The Real Story of Stuxnet" gives an overview of the attack chain and capabilities of the Stuxnet malware.
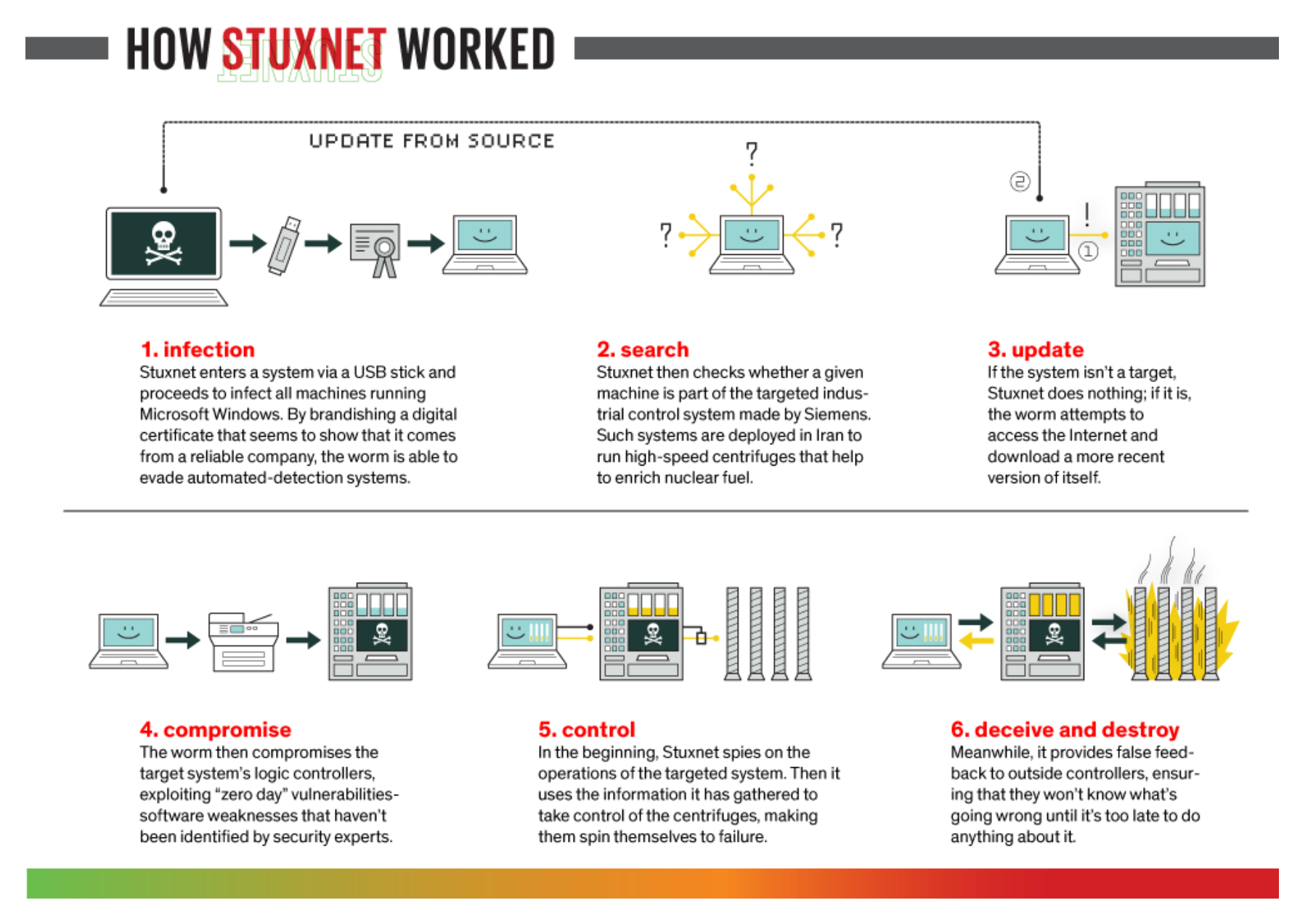
Immunity is the foundation of building advanced cyber capabilities. Without it, building sophisticated tools or setting up a structured organisation to conduct cyber operations would be impossible. However, an entity also needs resources to effectively leverage their immunity.
Resources
Like with most things in the world, opportunity is only one piece of the puzzle. In theory everyone has the opportunity to make millions of dollars on the stock market or crypto, but to do so you need resources to begin with. If you can only afford to invest $1,000 into a scam-coin, I mean, crypto-currency, even if you 10x your initial investment, you only make $10,000. But if you had $1,000,000, your gains would be exponentially higher. The same goes for building cyber capability - if an entity could legally conduct cyber operations, but only had 1 person to do it, their operations would be extremely limited. The more resources, the better the outcome. Resources can be money, labor, information or influence.
Consider a new cyber criminal operation - they don't have the immunity, but they decide to setup shop anyway. Their small operation starts making significant money extorting organisations with ransomeware. It's clear that their business model works so they want to expand. But they have a challenge. Firstly, who are they going to recruit? The pool of viable "talent" is relatively small. The talent pool for legitimate cyber security careers is already small, so imagine adding the fact that the job is illegal and you'll have to find a way to launder your salary. So even if they have the money to pay, they don't have a large enough talent pool to recruit and expand. Plus, don't forget that they are recruiting other criminals with questionable morals. If one of the new criminal recruits maliciously damages their operation, they have limited recourse and their business might be ruined.
On the flip-side, not only does the nation state have a legitimate operation, they also have a larger talent pool. They can invest the time and money to recruit and train people to help build their capabilities. In addition, they can vet their recruits to ensure their trustworthiness and if any of them step out of line they can come after them with the full force of the law.
The ability to expand resources is not only related to talent acquisition, it also applies to technology. Think back to the STUXNET example - to build malware to run on a specialised industrial control system without being detected or cause a catastrophic failure, they would need to have access to the same industrial control system to test their malware on before deploying it. So if you can't borrow a buddy's centrifuge or buy your own, the chances of building effective malware for the system are slim to none.
But what about simply buying capabilities? Surely buying spyware from a mercenary spyware developer like Paragon is a way to offload the need to have the resources required to develop your own advanced malware? Yes, that is true but tools like Pegasus are very expensive, costing millions of dollars and in theory are only sold to "good" governments. So you can't simply walk off the street and buy their tools. Plus, if organisations like Pegasus sell to criminals, they are likely to lose their lucrative government contracts.
Sophisticated Capabilities
So we can clearly see that nation states have the immunity and resources to build sophisticated cyber capabilities, but what does that actually look like? There are many factors that differentiate low-sophistication and high-sophistication threat actors but in general it boils down to skills, tools and infrastructure.
Skills
The skills of the people conducting cyber operations contribute to its sophistication. Like with any specialisation, an experienced practitioner will be able to more accurately and effectively complete their duties. They will have enough experience to identify weaknesses in networks, adapt to new situations, and recover when things go wrong. This allows them to operate swiftly and avoid being detected to effectively achieve their objectives. A novice is more likely to make mistakes, leave evidence behind or trigger alarms, possibly resulting in a security team response, which can easily compromise the entire operation. States have the luxury of longevity, such that they can rigorously train their staff in highly specialised fields.
Tools
Hackers use a variety of tools to conduct their operations. But not all tools are created equal. Some tools have more features and are more powerful, and others may simply be unique enough to go undetected. Nation states are likely to use custom, one-of-a-kind tools, with advanced features that have never been seen before (such as the STUXNET example earlier). These tools are not only specialised and effective, but are also hard to detect. Virus and malware detection systems still rely heavily on unique patterns or "signatures" to detect malicious files and applications, so if they have never been seen before, the anti-virus software will not be able to detect it.
Infrastructure
Conducting cyber operations also relies on the Internet's infrastructure. While it may feel like the Internet is an ambiguous cloud, it is made up of servers, network devices, physical cables, and satellites connecting everything together. To use the Internet you have to connect via an Internet Service Provider (ISP) and then you can visit a website hosted on someone else's server or host your own website on your own server.
For a law abiding citizen, this is relatively easy. You simply call an ISP of your choice who will connect you to the Internet. Then you can use one of many online providers to buy your domain name, rent some servers and storage or use a cloud service. However, for these service providers crime is (usually) bad for business, so getting access to their services is not as simple for a criminal. In contrast, the power and control a government can have over domestic service providers means they have access to the best infrastructure and other systems not available to the public and they can even have service providers give them special assistance in their operations.
Conclusion
The difference in immunity and resources between criminal and state sponsored cyber operations results in the two having significantly different capabilities. Whether that's by being able to recruit and train personnel, develop sophisticated capabilities, or have access to the infrastructure needed to conduct their operations. But as the saying goes, "its not about the size, its about how you use it". So in the next part of this series we will take a look at the different objectives and tactics employed by criminals and nation states. Until next time, stay safe.
Member discussion